In this article, we will give you an overview of China PIPL and uncover how exactly your business is involved as a data controller, data processor, or both. You will also learn how IT Consultis take these complexities into account when offering digital transformation services to the most ambitious brands in China.
DISCLAIMER:
Please be aware that the information in this blog article does not, and is not intended to, constitute legal advice regarding the Personal Information Protection Law (PIPL) of the People’s Republic of China (PRC) as well as other relevant laws and draft rules mentioned.
Although well researched, all information and materials in this article only serve as a general guide to help you understand the PIPL’s implications on your business while operating in and/or working with the China market.
Any suggestions made are based on our partner TEKID’s expertise and ITC’s experiences as a Shanghai-based digital transformation consultancy that helps clients navigate the digital landscape in China.
It should also be noted that the PIPL and related rules will continue to evolve going forward. Thus, this article may not be fully relevant or exact in the future.
Introduction
Over the past decade, the Authorities in China have been taking cybersecurity and data privacy protection more seriously to govern the power of the private tech giants within the country as well as multinational companies profiting off of its over-a-billion consumer market.
And the recent introduction of the China PIPL is one of the first steps to crack down on this issue and enhance consumer protection. As a result, the operations of many businesses inside and outside of China have been affected.
However, these complexities are not the end of the world. Brands can still further expand their digital presence and operations in China, as long as they learn how to stay compliant as a data controller and/or data processor.
First, let’s take a look at what this law entails:
Table of Contents
What is the China PIPL?
The new China Personal Information Protection Law sets the regulatory framework, including enforcement mechanisms and penalty guidelines, to instruct companies on how they must handle personal data.
The most notable point is that it is applicable to all entities that process data from China (more will be explained below).
Companies that fail to comply with PIPL will face serious punishments, including fine impositions reaching as high as RMB 50 million (around $7.5 million) or 5% of the company’s previous annual revenue.
PIPL was first passed on 20 August 2021. Companies everywhere then had had 2 months to prepare how to navigate the new data protection law until it took effect on 1 November 2021.
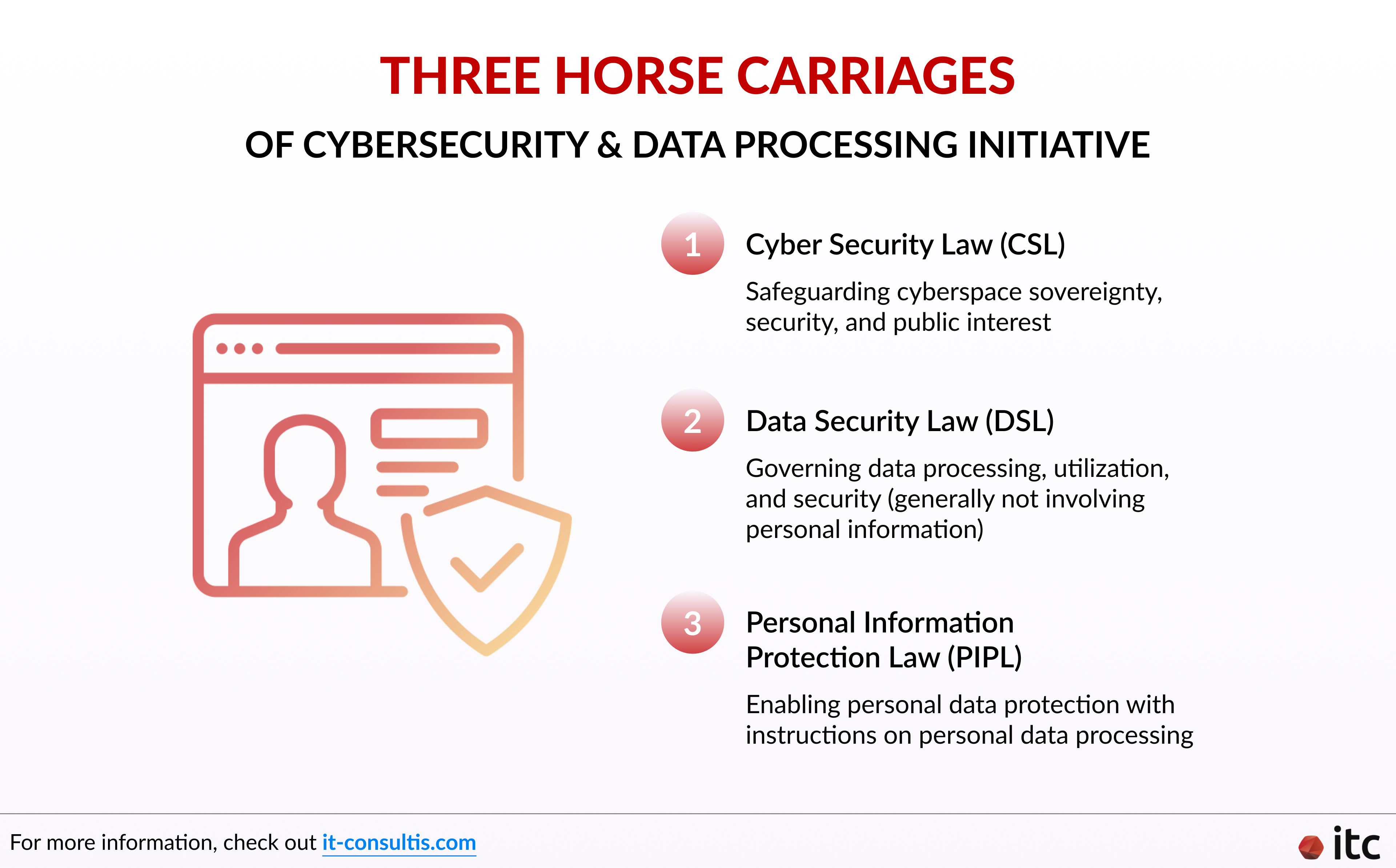
It is actually a part of the country’s overarching cybersecurity and data processing initiative. This is called the “Three Horse Carriages”, which consists of:
- The Cyber Security Law (CSL) (June 2017 – for safeguarding cyberspace sovereignty, security, and public interest)
- The Data Security Law (DSL) (September 2021 – for governing data processing, utilization, and security that generally do not involve personal information)
- The Personal Information Protection Law (PIPL)
What is Personal Data under PIPL?
According to the official English translation of the Personal Information Protection Law (for reference only) released by the National People’s Congress of the People’s Republic of China (PRC) in December 2021:
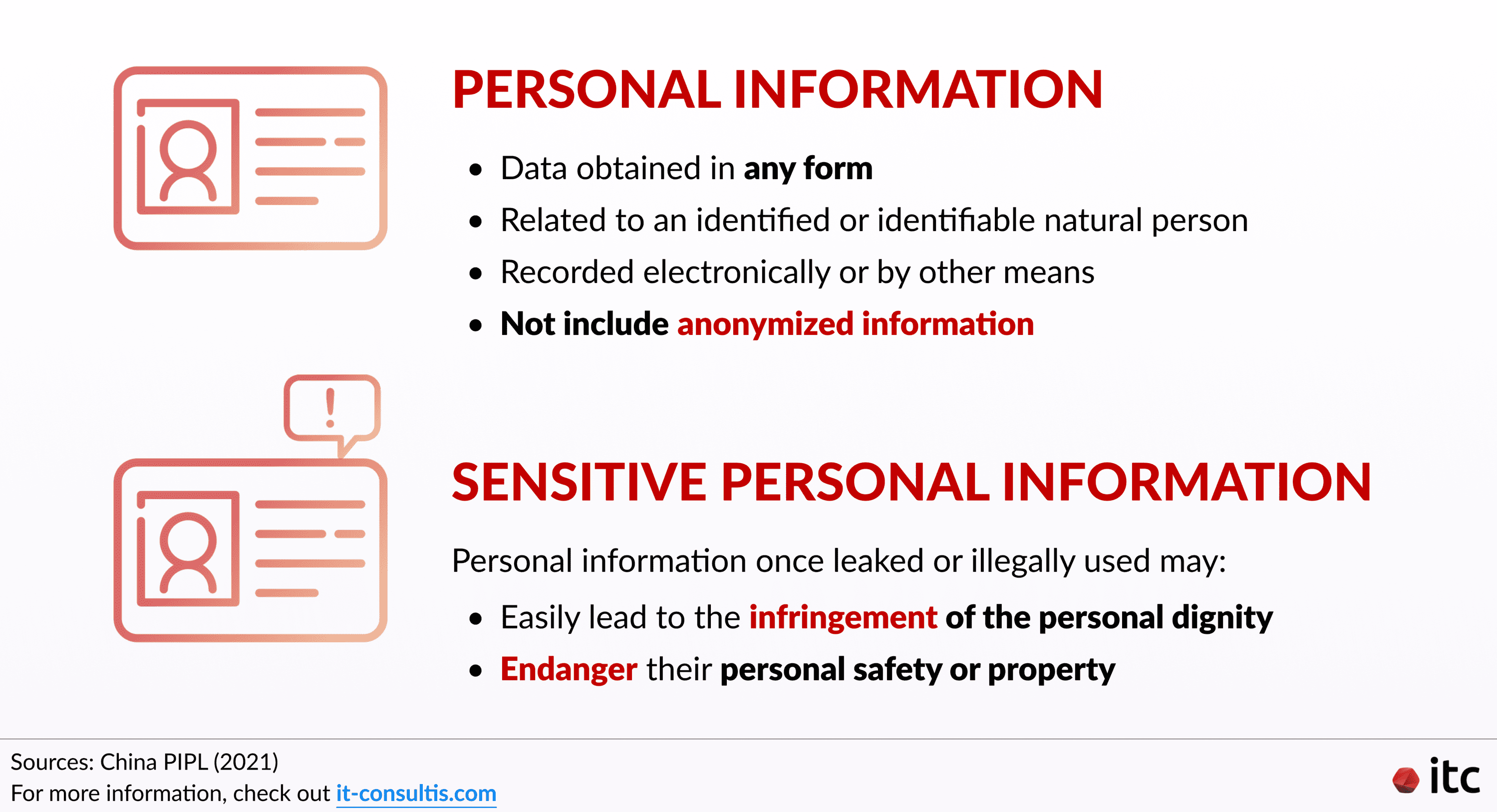
“Personal information refers to various information related to an identified or identifiable natural person recorded electronically or by other means, but does not include anonymized information.”
“Various information” here can be understood as data obtained in any form, including “video, voice, or image“.
And “anonymized information” simply refers to pieces of data that have been processed to “make it impossible to identify specific natural persons and impossible to restore”.
What is Sensitive Personal Data in China?
The same governmental source also clarifies the definition of “sensitive personal information” as “personal information that once leaked or illegally used, may easily lead to the infringement of the personal dignity of a natural person or may endanger his personal safety or property“.
This includes information such as “biometrics, religious belief, specific identity, medical health status, financial accounts, and the person’s whereabouts, as well as the personal information of a minor under the age of 14 years”.
Who does China’s PIPL Apply to?
China PIPL brings up the concept of “personal information processors” for the first time ever.
The law applies to all personal information processing entities and/or entrusted parties that process information of natural persons within the territory of the PRC. This includes both domestic and multinational and foreign companies operating within or outside the territory of the country, for any of the following purposes:
- Providing products/services for natural persons residing in China
- Analyzing or assessing the behaviors of people living in China
- Other circumstances as provided by any law/administrative regulation
In particular, the law also specifies that personal information processing encompasses “personal information collection, storage, use, processing, transmission, provision, disclosure, and deletion, among others”.
Why Should You Care?
Global Impact
As mentioned above, as long as your company processes personal data acquired from China, you will very likely have to comply with the PIPL. Thus, virtually any entity around the world can be impacted by the law. And this also includes third-party data processors with no business presence in China.
Increased Risks and Costs
Due to the Authorities’ strict impositions to protect users’ data privacy, businesses everywhere have to deal with an increase in costs to mitigate related risks and ensure compliance with the law.
This includes considerations for cross-border data transfer and data localization.
But before diving into these aspects, you need to understand the differences between the roles of a Data Controller and a Third-Party Data Processor:
Data Controller vs Data Processor
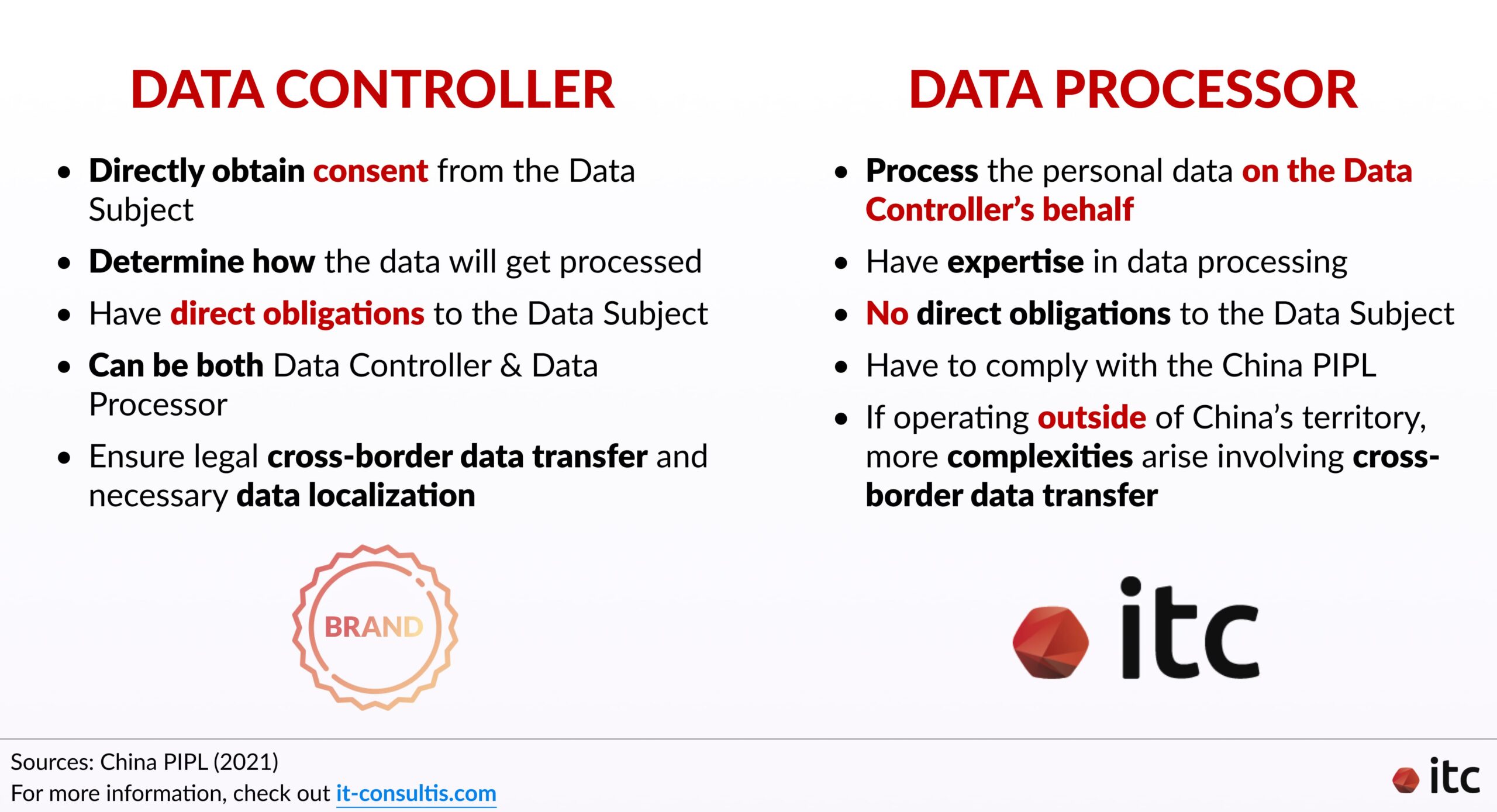
Data Controller
These are entities that directly obtain consent from the Data Subject and determine how the data will get processed. Thus, these companies have “direct obligations to the Data Subject“, according to Maxime Oliva, CEO of TEKID – a Digital Risk & Security advisory firm.
A data controller can also simultaneously be a data processor. They can process the obtained personal information themselves if they adhere to the following general guidelines:
- Only process personal data when it is necessary for directly-related explicit and reasonable purposes.
- The process should impose minimum impact on the rights and interests of individuals in China.
- Processors have to transparently disclose the rules for processing personal information, along with its purposes, means, and scope (e.g., clear Terms & Conditions)
- Guarantee the quality of personal information involved in the process.
- No illegal collection, usage, processing, transmission, trading, provision, disclosure of others’ personal data, or engagement in processing activities that can endanger national security or harm public interests.
Third-Party Data Processor
However, many companies do not process the data alone. They also work with third-party data processors who do so on their behalf. This way, the data controllers can make the most out of the data by benefiting from external expertise.
For instance, IT Consultis (ITC) is a third-party data processor. We provide an array of services to power ambitious brands’ digital transformation journey in China.
Thus, we work with clients’ data often to help them devise and implement effective strategies that maximize their ROI (more will be explained below).
Though third-party data processors do not have direct obligations to the customers, they still have to comply with the China PIPL. And more complexities arise if they operate outside of China’s territory as personal information needs to be transferred across the border.
Cross-Border Data Transfer and Data Localization for Multinational Companies
Cross-Border Data Transfer
At ITC, we have worked with many global brands with a branch in China. And it is certainly not unusual for them to transfer the data collected domestically back to their global headquarter in another country to holistically process them.
Additionally, some brands may also transfer data to third-party data processors based abroad, as explained earlier.
Fortunately, China PIPL still enables many brands to share information across the border via either of the following 3 main legal pathways:
- Passing the National Cyberspace Department’s Security Assessment
- Obtaining the Personal Information Protection Certification from a relevant institution
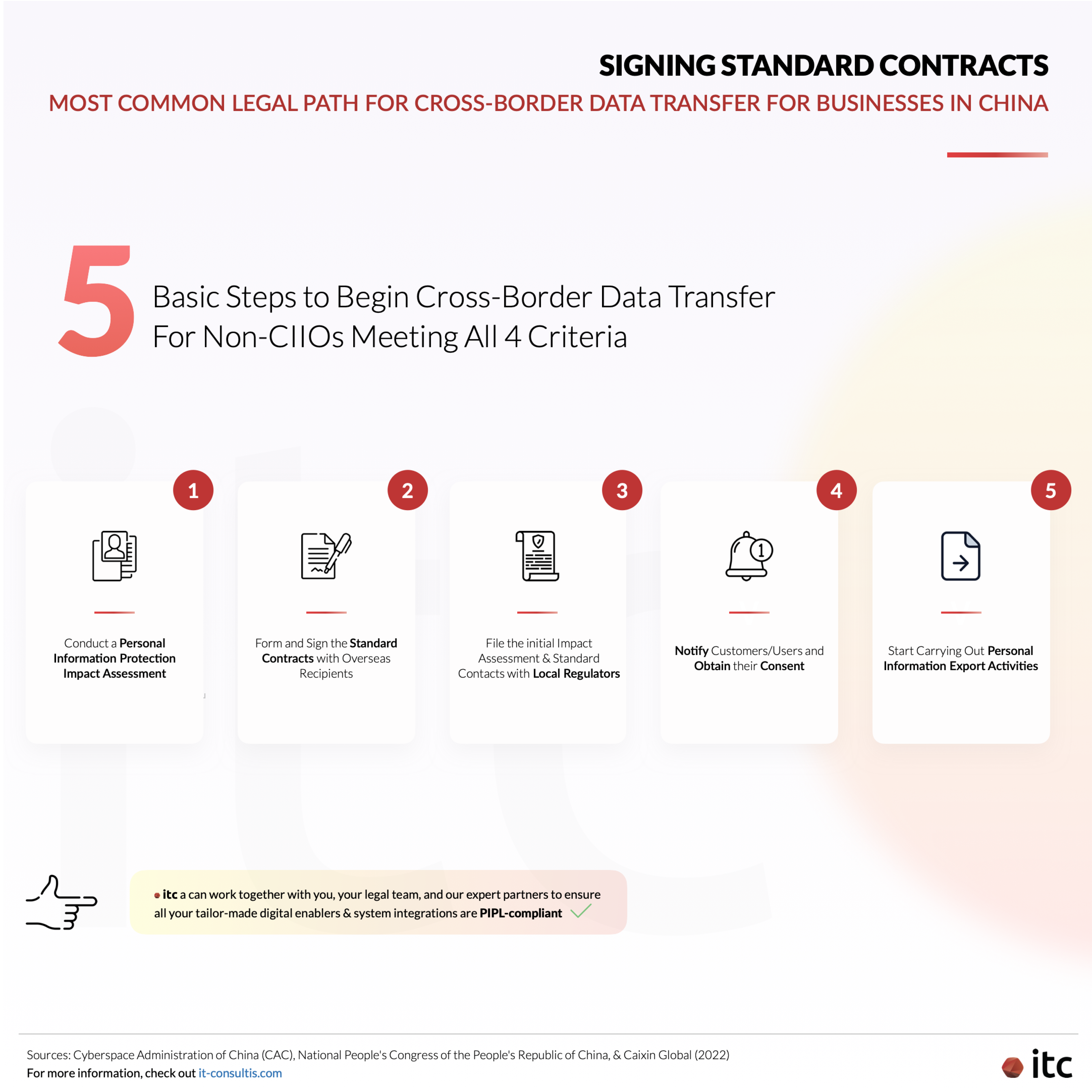
- Signing a Standard Contract stipulating rights and obligations with the overseas recipient
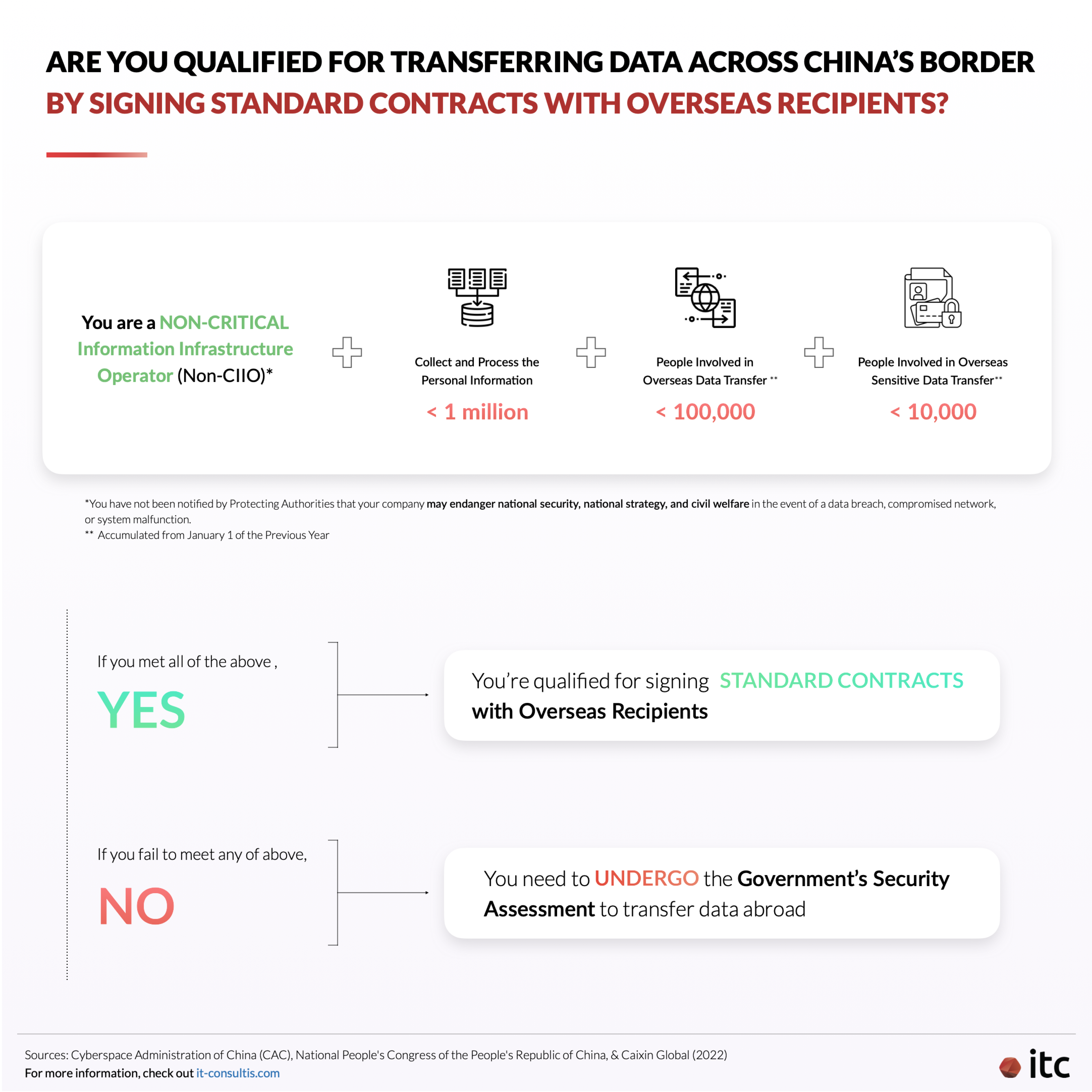
Among them, the last option is considered to be a more standard practice globally and the most feasible out of them all. To sign Standard Contracts, you need to meet the following 4 criteria:
- You are a Non-Critical Information Infrastructure Operator (Non-CIIO) and Data Processor
- You collect data involving fewer than 1 million people
- Since January 1 of the previous year, you have transferred overseas personal information involving fewer than 100,000 people
- Since January 1 of the previous year, you have transferred overseas sensitive personal information involving fewer than 10,000 people
Unsure whether you are a CIIO or not? Do not worry!
The regulatory departments are responsible for identifying and notifying CIIOs. And these entities typically engage in important industries or fields like public communication and information services, energy, and finance.
Hence, if you are a typical retail brand building eCommerce channels in China like many of ITC’s clients, rest assured that you meet the 1st criterion.
And, should you fail to meet any of the above criteria, you will need to apply to the National Cybersecurity and Information Department and undergo their security assessment to qualify for cross-border data transfer.
Data Localization
CIIOs work with important information that, once lost or leaked, can seriously endanger national security, national economy, and civil welfare.
Thus, to enhance cybersecurity and data security protection, the China PIPL requires CIIOs to 100% store personal data within Mainland China.
You may still be allowed to share data abroad, but only after you have successfully passed the Authorities’ security assessment mentioned above.
PIPL and Digital Transformation – How ITC Helps Ensure Compliance
As previously mentioned, ITC is a digital transformation consultancy that can be considered a third-party data processor as our services involve dealing with the clients’ obtained data from consumers.
Having worked with 600+ domestic and multinational brands on their digital transformation journey in China, ITC has become well-versed in how we can assist brands with their PIPL obligations together with their legal team and our expert partners, such as TEKID. Particularly:
Drafting Data Policy & Transparency Reports
Maxime, our expert partner on Cyber Security, also noted that brands need to address all visible elements as soon as possible, as that is what the users (and the Authorities) would access and interact with first. Specifically, work hard on the Privacy Policy and Terms and Conditions.
ITC can help you draft these policies to protect the users’ privacy and rights to their data as well as your business’s rights in case of abuse and litigation.
They should be easy to find and transparently, accurately, and straightforwardly inform the users of:
- The name and contact information of the data processor
- The purposes and means of personal information processing along with its categories and storage periods
- The methods and procedures for the individual to exercise their rights
- Other matters that they should be notified of according to the laws and administrative regulations
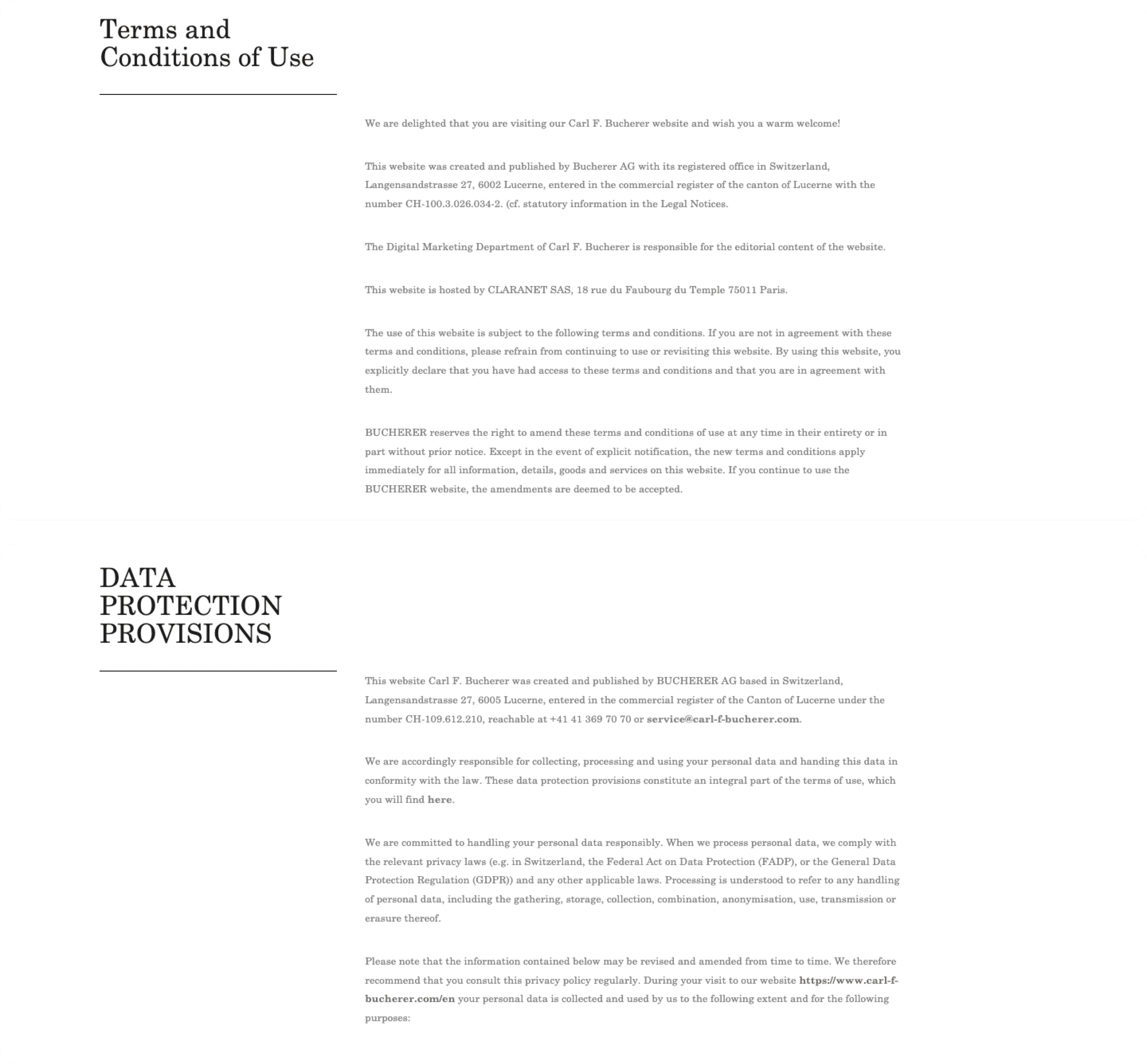
For example, in addition to a Terms and Conditions of Use page, Carl F. Bucherer, a luxury Swiss watchmaker, also dedicated a Data Protection Provisions page to ensure compliance with the local and global data privacy regulations, including China’s.
Here, the brand detailed clearly its contact information as well as the extent and purpose of its collection, processing, and use of personal data.
Obtaining Consent from Customers
IT Consultis can also help your company obtain consent for data capturing, processing, and exporting activities via methods such as opt-in checkboxes.
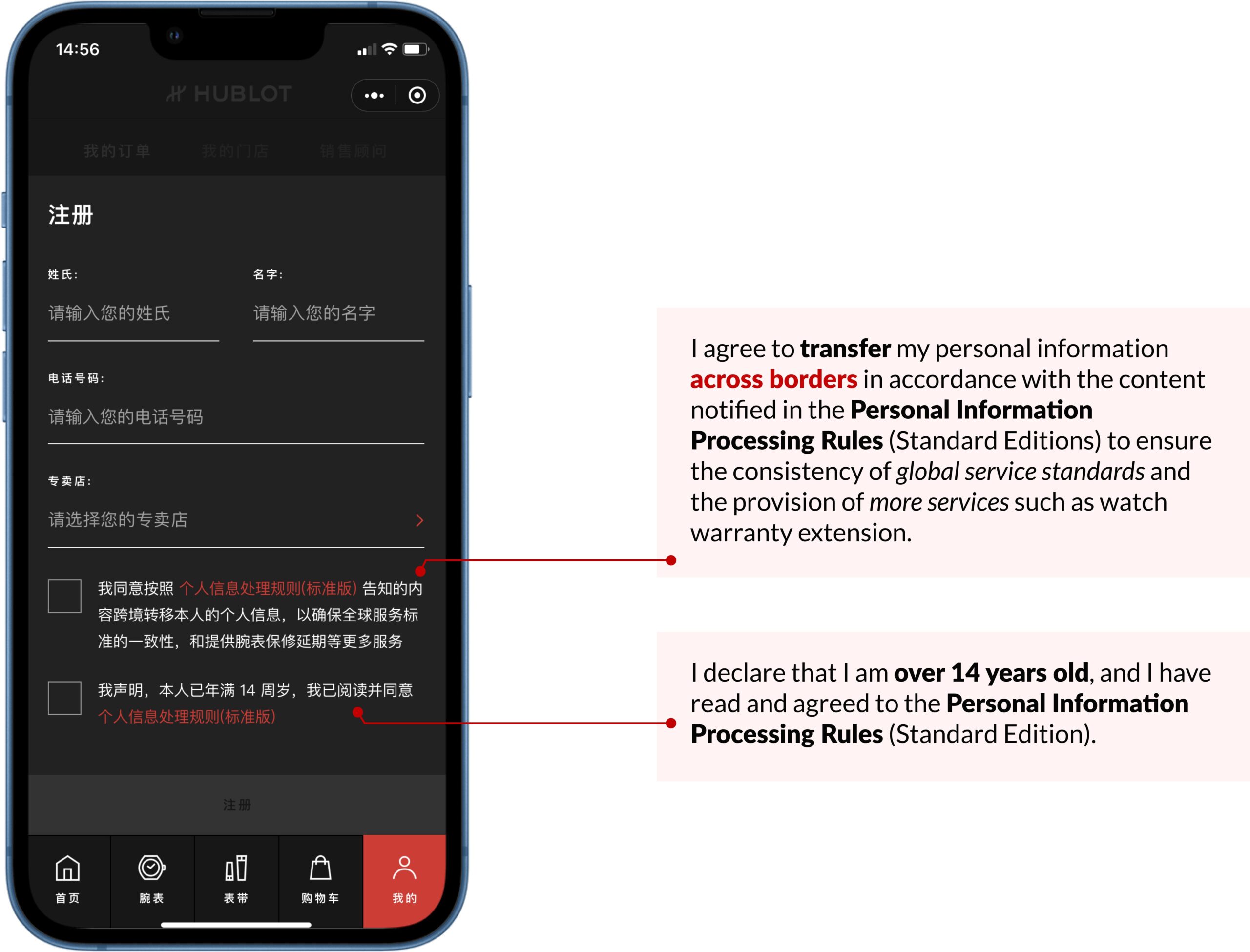
If we are designing your bespoke digital enablers (e.g., WeChat Mini Program, website, app, H5, etc.), ITC will make sure that they are clear and well-positioned. This way, “the individual consent shall be voluntary, explicit, and fully informed”, per Article 14 in the China PIPL.
For instance, the WeChat Mini Program of Hublot, an LVMH subsidiary Swiss luxury watch brand, asks users to read and consent to its Personal Information Processing Rules, including cross-border data transfer, before registering for an account.
This way, Hublot can effectively capture valuable data while users can opt-in to enjoy universal service standards along with additional benefits like a watch warranty extension.
In addition, if the user would like to withdraw their consent later on, ITC will also help our clients ensure that the process is designed to be as simple and convenient as possible, without compromising customers’ reception of products and services.
Analyzing Data & Automating Decision-Making Processes
As a digital transformation consultancy, we also work directly with the data often as a data processor to:
- Create personalized Marketing Automation journeys
- Power clients’ Social CRM systems
- Enable effective internal collaboration and external communication with customers via WeCom
- Devise omnichannel loyalty programs
Due to the Authorities’ crack-down on personal data transfer and processing, it is harder to pull out secondary and third-party data. Thus, businesses need to acquire more first-party data from private traffic domains like WeChat Official Account and Mini Program, which enables 100% data ownership.
Here, brands also have the home advantage – they can clearly communicate with users their processing intentions and approaches to gain consent, including automated decision makings with Marketing Automation, Social CRM, and WeCom.
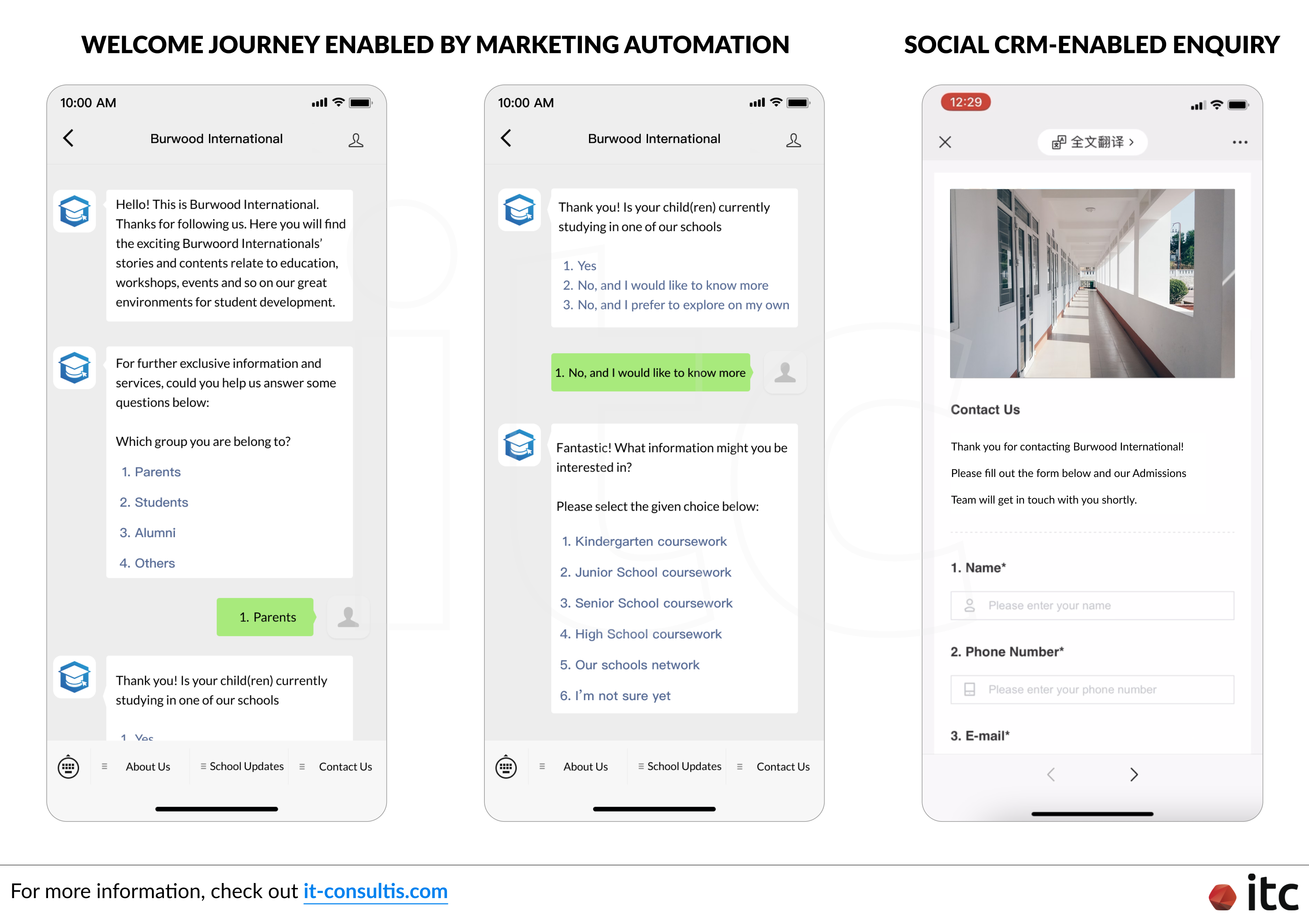
When assisting a leading Education Group in Asia with recruiting students from China, IT Consultis plugged the school’s WeChat Official Account with a Social CRM tool to effectively nurture leads.
Our strategies involved collecting key data from users, automatically processing them based on a customized Lead Scoring System, and profiling them into different groups of prospects.
And, to comply with Article 24 of the China PIPL, the Group needs to provide explanations about automated decision-making (e.g., information and marketing push) and offer non-personalized options when necessary to ensure transparency and fairness.
Cross-Border System Sync-Up/Integration
As previously mentioned, many of our clients demand globalization services that enable data sync-up between their Chinese and global systems. At IT Consultis, we offer digital system integration services to ensure seamless data circulation, display, and tracking.
However, due to PIPL, it is not a simple process. Although ITC is not a legal expert, based on our past experiences, we can recommend certain directions you should take regarding aspects like data hosting, data localization, and what exactly can be sent abroad.
This way, where possible, your global and local digital systems can intelligently communicate with each other while staying PIPL-compliant.




